ONE (of the who knows how many) backdor discovered by accident on open source software.
Not all distributions. And there are patches available. Windows and McOS having similar issues. But never patched until today. Microsoft by sefld has a problem. And no solution for it. So what? No security in Linux world? Ahh, I’m sorry. It is still secure.
no need for a pissing contest
the malicious version wasnt widely distributed - yet - but the fact that a carefully crafted malicious bit of code made it into such a widely used utility is … worrisome
it sounds like it was a long term plan to infiltrate the security of linux
Goot to know that you review every single line of code of every single open source tool, library, distro… to be 100% sure that it is safe ![]()
Good toknow that you ignore that every System has problems like this. And no, I am not reviewing every line of Code. Do you review every change on Darwin Sources used by apple for macOS and others? I guess no. Exactly that IS the point. You can’t. But there is not even the chance if you have nobody looking into the Sourcecode. That makes different problems. This backdoor is not a problem of all and also not of the most distributions. But okay, I can live with this wording.
Anyhow the Linux OS is secure. After patching it is even more. And not all installs with that backdoor are exposing the backdoor.
the pissing match can stop ANY time now
I am sorry for that but I am not accepting to let me look on that and not react.
Linux is a secure OS but as user base grows, it’s gonna get attacked a lot more. Also, it’s user’s responsibility to keep it secure. There already exists interesting hard to detect malware targeting Linux, like “Symbiote”.
Yes but like you wrote: the user is in charge of keeping it secure. That’s normal. For Linux. For Windows. For macOS. Clicking on every link getting via Mail for example is not a good Idea. Typing in the password every time an installer wants it is not helping: look what you are doing. And yes, being careful is a real good advice for all operating systems. Even on mobile phones it is a good advice.
The spotted backdoor is a problem. And already in patch. Also not all Linux bistros delivering it. And the ones which re delivering it are all unstable branches. The stable branches are not containing it. So for me is the question: where is the real world problem?
If this backdoor would be in macOS or Windows it would not be found out! Cause nobody would be able to find an real analyze it. The next is: who the heck has ssh switched on? This backdoor is ssh related. So it is mostly a server problem. It could be really dangerous. But nothing happened. I doubt that this chance would be given when and if that would be on macOS? Who knows.
But it shows something else: the fact that Linux became target like macOS and Windows. So Linux users are not anymore in this “nothing can be happened” hybrid and have to take care for their systems.
sigh another biased and panic making video, with dramatic music and sfx… turned it off after 20 Sec
the xz incident shows great advantage of Open Source Software. Because for Closed Source you will never know anything about backdoors (Cisco frequently is patching its crap because of hard coded root access somewhere in his components).
Imagine, for over 5 years Mr Jia Tan tried to gain the trust of the Maintainer of an small Lib. First he gave some commits, patches and updates in cooperation with others and got finally maintaining rights for this project. Mostly because his fake accounts pushed the original maintainer, who did this as hobby/ side project. And then after five years of this hard labour he commits a nasty backdoor, which is immediately discovered by a Debian maintainer in the experimental (sid) branch of Debian. Everybody who is on sid, knows (ord better should know, what he/she is doing). Of course some rolling releases patched it in their repo aswell (again everybody who is on rolling releases should know, what he/she is doing). Hence all stable and old-stable Debian Releases are not effected.
Bottomline: XZ is a success story of how Open Source and Peer Review can prevent us from evil actors. This happens in the academic world more often when papers are pushed in and peer-reviews debunk them.
And Software Developers, who just copy and paste or linking every crap, should better shut up… they are building castles in the sky… this xkcd says it all:
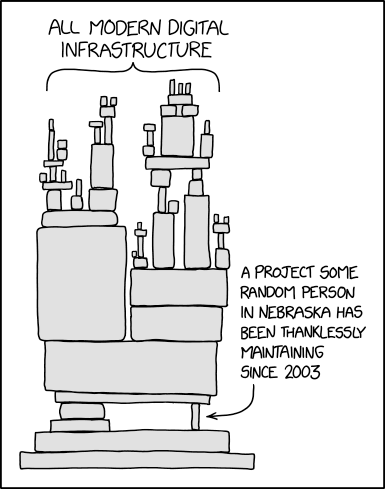
ah forgot our running gag…
Linux Dev finds a 500 ms lag in SSH… and discovers a backdoor…
MS Dev finds a 500 ms lag in MSTeams… and nobody cares…
As i understood only systems with systemd is affected. (attack strategy: systemd->liblzma->sshd) So macOS is not the target in this case.
Yeah the write ups about how this attack worked are quite clever
And I dont think they apply to macOS from how this works
I spoke about similar and not the same. The entire problem is that mostly you will not get any information about. only if somebody uses it. that is exactly what i describe. the linux bug is not the only one we will find and correct.
